Can AI give me super vision?
This Week’s featured Blog
Installing DNS from scratch on a Windows Server
1 3This content is from our CompTIA Network + Video Certification Training Course. Start training today! In order for you to be able to use DNS, if you’re going to use it on an on‑premise environment, which means internally, or if you’re going to set it up as a cache‑only DNS server, one of the first … Continue reading Installing DNS from scratch on a Windows Server
Can AI give me super vision?
0 2I recently received the Grove-Vision AI from Seeed StudiosA to explore. I decided to blog about my experience. First off, full disclosure, they sent this to me to check out – I did not cough up the enormous $25 purchase price. 😊 It is a small package at ≈ 19/16″ x 3/4″ (4cm x 2cm), … Continue reading Can AI give me super vision?
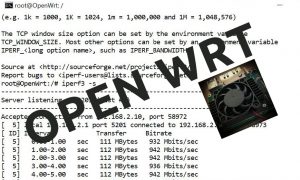
How to install OpenWRT on a Raspberry Pi Compute Module 4
0 1Some time ago I wrote a blog which mentioned OpenWrt. I have also written about the joy of doing projects the various Raspberry Pi units over time, so this blog combines two of my favorite IT topics. I now have another device which runs OpenWrt, so I thought I would share my experiences. This device … Continue reading How to install OpenWRT on a Raspberry Pi Compute Module 4
How to subnet an IPv6 network – a 48 block example
0 0An IPv6 subnetting example: You are issued a /48 block from your ISP. Subnet it so you have more than 500 networks. Red numbers are the original 48 bits of the network issued by your ISP. The red bits do not change in this example. Must borrow 9 more bits (29 > 500) to get … Continue reading How to subnet an IPv6 network – a 48 block example
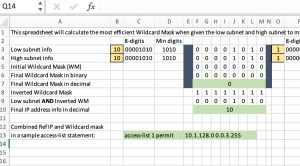
How to Construct a Wildcard Mask to Match a Range of Subnets – Plus Download the Spreadsheet Tool
0 2How often have you been creating an ACL and you needed to match not ONE subnet, but a whole range of subnets? The same logic holds for creating a “network” statement in an IGP such as EIGRP or OSPF. You want a single statement to match all your desired subnets, but you don’t want your … Continue reading How to Construct a Wildcard Mask to Match a Range of Subnets – Plus Download the Spreadsheet Tool
The Easy Way to Convert Decimal Numbers to Binary Numbers and Back Again
0 3Converting from one number base to another. Riveting stuff! But if you want to have confidence in your skills as A+, Network+, or CCNA certified, you don’t want to overlook this seemingly small area of study. It is quite important because humans like to look at decimal (base 10) numbers, whereas computers work with binary … Continue reading The Easy Way to Convert Decimal Numbers to Binary Numbers and Back Again
COVID-19 UPDATE: Microsoft Extends Deadlines for Exams and Certifications!
0 0At Interface, we are working closely with Microsoft to help our customers adjust and manage daily work as the coronavirus continues to affect our professional and personal lives. Today, we want to share an update on the steps Microsoft has taken to adapt to the current environment and what that means for you as our … Continue reading COVID-19 UPDATE: Microsoft Extends Deadlines for Exams and Certifications!
Project Management (PMP) for Executives – Introduction
1 96 0Introduction Project Management (PMP) for Executives is a 9 part video training series developed by Steve Fullmer, PMP, MBA, MCT/CTT+, CDP. Steven has a global reputation as a project manager, chief technology officer, and computer systems innovator. He has authored more than 100 articles and a dozen courses in the fields of project management, productivity, business … Continue reading Project Management (PMP) for Executives – Introduction
Project Management (PMP) Leadership Skills in the 21st Century … Do you Know Your History? – November 10, 2017
0 99 2The PMI Leadership triangle touts our need to develop our knowledge and application of leadership. Do you understand the leadership models of the 20th century? The 21st Century? Understanding your predecessors can assist to set your future course. On the matter of history, Mark Twain’s quote “History doesn’t repeat itself, but it does rhyme” is … Continue reading Project Management (PMP) Leadership Skills in the 21st Century … Do you Know Your History? – November 10, 2017
Principles of Decision Tree Design and Analysis in Project Management (PMP)
0 59 0In this Project Management Professional (PMP) training video, learn how about Decision Trees and how to solve them with Risk Analysis. Existentialism conveys themes like the importance of choice, contingencies, and extreme situations. How do you choose when the decision is hard? (If the decision is easy, you just choose.) When the decision is hard, we … Continue reading Principles of Decision Tree Design and Analysis in Project Management (PMP)
Understand the Mind to Become a Better Project Manager – February 18, 2015
0 98 2Our minds all work alike, at least biologically. Yet we are a diverse species with different motivations, opinions, perspectives, and directions. Do you understand how and why the human mind works? What makes you a great project manager? In this recording of our PMP training webinar from February 18, 2015, Steve Fullmer covers some of … Continue reading Understand the Mind to Become a Better Project Manager – February 18, 2015
Windows 10 Security – What’s New and Improved? – December 3, 2015
0 104 1In this recording of our Windows 10 webinar from December 3, 2015 training, security expert Mike Danseglio presents the enhanced security features of SmartScreen, Defender and BitLocker in Windows 10 and new features such as Biometric Identification, Microsoft Passport, Device Guard and more.
Windows 10 Managing, Deploying and Configuring – December 2, 2015
0 486 1In this recorded Windows 10 training webinar from December 2, 2015, Windows Server instructor Rick Trader presents the deployment and management of Windows 10 Enterprise and the new Provisioning capability in Windows 10. Learn how to manage Windows 10 deployments using System Center Configuration Manager, Mobile Device Management and Intune. Also included in his presentation … Continue reading Windows 10 Managing, Deploying and Configuring – December 2, 2015
Project Management (PMP) for Executives – Introduction
1 96 0Introduction Project Management (PMP) for Executives is a 9 part video training series developed by Steve Fullmer, PMP, MBA, MCT/CTT+, CDP. Steven has a global reputation as a project manager, chief technology officer, and computer systems innovator. He has authored more than 100 articles and a dozen courses in the fields of project management, productivity, business … Continue reading Project Management (PMP) for Executives – Introduction
Project Management (PMP) Leadership Skills in the 21st Century … Do you Know Your History? – November 10, 2017
0 99 2The PMI Leadership triangle touts our need to develop our knowledge and application of leadership. Do you understand the leadership models of the 20th century? The 21st Century? Understanding your predecessors can assist to set your future course. On the matter of history, Mark Twain’s quote “History doesn’t repeat itself, but it does rhyme” is … Continue reading Project Management (PMP) Leadership Skills in the 21st Century … Do you Know Your History? – November 10, 2017
Principles of Decision Tree Design and Analysis in Project Management (PMP)
0 59 0In this Project Management Professional (PMP) training video, learn how about Decision Trees and how to solve them with Risk Analysis. Existentialism conveys themes like the importance of choice, contingencies, and extreme situations. How do you choose when the decision is hard? (If the decision is easy, you just choose.) When the decision is hard, we … Continue reading Principles of Decision Tree Design and Analysis in Project Management (PMP)
Understand the Mind to Become a Better Project Manager – February 18, 2015
0 98 2Our minds all work alike, at least biologically. Yet we are a diverse species with different motivations, opinions, perspectives, and directions. Do you understand how and why the human mind works? What makes you a great project manager? In this recording of our PMP training webinar from February 18, 2015, Steve Fullmer covers some of … Continue reading Understand the Mind to Become a Better Project Manager – February 18, 2015
Windows 10 Security – What’s New and Improved? – December 3, 2015
0 104 1In this recording of our Windows 10 webinar from December 3, 2015 training, security expert Mike Danseglio presents the enhanced security features of SmartScreen, Defender and BitLocker in Windows 10 and new features such as Biometric Identification, Microsoft Passport, Device Guard and more.
Windows 10 Managing, Deploying and Configuring – December 2, 2015
0 486 1In this recorded Windows 10 training webinar from December 2, 2015, Windows Server instructor Rick Trader presents the deployment and management of Windows 10 Enterprise and the new Provisioning capability in Windows 10. Learn how to manage Windows 10 deployments using System Center Configuration Manager, Mobile Device Management and Intune. Also included in his presentation … Continue reading Windows 10 Managing, Deploying and Configuring – December 2, 2015
A Simple Introduction to Cisco CML2
0 3901 0Mark Jacob, Cisco Instructor, presents an introduction to Cisco Modeling Labs 2.0 or CML2.0, an upgrade to Cisco’s VIRL Personal Edition. Mark demonstrates Terminal Emulator access to console, as well as console access from within the CML2.0 product. Hello, I’m Mark Jacob, a Cisco Instructor and Network Instructor at Interface Technical Training. I’ve been using … Continue reading A Simple Introduction to Cisco CML2
Creating Dynamic DNS in Network Environments
0 645 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader teaches how to create Dynamic DNS zones in Network Environments. Video Transcription: Now that we’ve installed DNS, we’ve created our DNS zones, the next step is now, how do we produce those … Continue reading Creating Dynamic DNS in Network Environments
Cable Testers and How to Use them in Network Environments
0 731 1This content is from our CompTIA Network + Video Certification Training Course. Start training today! In this video, CompTIA Network + instructor Rick Trader demonstrates how to use cable testers in network environments. Let’s look at some tools that we can use to test our different cables in our environment. Cable Testers Properly Wired Connectivity … Continue reading Cable Testers and How to Use them in Network Environments